
Psychz - Anup
Votes: 0Posted On: Oct 10, 2018 04:38:03
Linux machines by default offer you a certain level of security and are immune to threats that usually can affect any other operating systems. However, due to increasing cyber threats today, it is highly recommended and wise to configure a firewall on your Linux server.
There are other few options where you can where you can configure firewall whereas Iptables is most commonly preferred as it comes preinstalled on all of the Linux distros.
Iptables is an effective firewall that provides protection from simple attacks. Iptables provides IPv4 packet filtering and NAT, which facilitates traffic filtering and blocking.
iptables almost always comes pre-installed on any Linux distribution. To update/install it, just retrieve the iptables package:
sudo apt-get install iptables
iptables uses three different chains: Input, Forward, and Output.
Input - Controls the behavior for all incoming connections. This monitors any user that attempts to SSH into your server machine. It will verify the attempt against the rule in the input chain and validate the connection.
Forward - This monitors incoming connections that aren’t actually being delivered locally. This chain is hardly used unless you are you are using the server for routing or NATing purpose that requires forwarding.
Output – This monitors all the outgoing connections. All the outgoing requests or connections will go through a rule that is defined here and verify
You can add rules once your chain policies are in place. By adding rules to the iptables, you can have control over connections from particular IP address or to port.
Basically, there are three commonly used responses "Accept", "Drop", and "Reject"
As the name suggests, Accept allows a connection to establish, Drop simply drops the connection so no trace of it would be found. And finally, Reject which does not allow connection and throws an error.
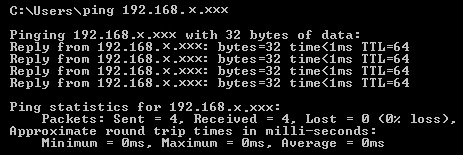
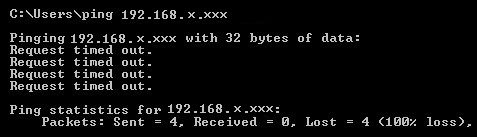
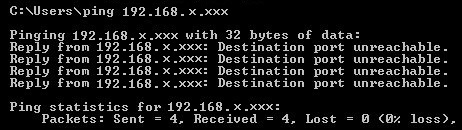
A simple example using a ping command can show results in each of the tree cases. Following are the outputs in each
Accept
Drop
Reject
Now, to your query, allow 192.168.0.1 on port 3306, port 22 and block everyone else. You can use the following entries to add it in the iptables to do the job
iptables -I INPUT 1 -p tcp -s 192.168.0.1 --dport 3306 -j ACCEPT
iptables -I INPUT 2 -p tcp --dport 3306 -j DROP
iptables -I INPUT 3 -p tcp -s 192.168.0.1 --dport 22 -j ACCEPT
iptables -I INPUT 4 -p tcp --dport 22 -j DROP
Note: In these examples, we’re going to use iptables -I to rules to the existing chain. iptables starts at the top of its list and goes through each rule until it finds one that it matches. If you need to insert a rule above another, you can use iptables -I [chain] [number] to specify the number it should be in the list.