Reference Architecture - Dedicated Server Deployment
Publisher: Psychz Networks, September 07,2023- Introduction
- Hardware Consideration
- Architecture Diagram
- Network Configuration
- Software and OS Installation
- Security Measures
- Backup and Recovery
- Scalability and High Availability
- Maintenance and Monitoring
- Conclusion
Introduction
This document serves as a comprehensive guide for deploying bare metal servers within our infrastructure. It is designed to standardize the deployment process, minimize human error, and ensure efficient, secure implementations that adhere to industry best practices.
It is intended for Infrastructure Teams, System Administrators, DevOps Teams, Security Teams, as well as Management and Leadership, providing them with a structured approach to seamless and reliable server deployment.
Hardware Considerations
Components
A variety of 5th, 4th, and 3rd Gen Intel Xeon Scalable processors, Intel Xeon processor, Intel Atom processors, Intel Data Center GPU Flex Series, and Intel Arc™ Series GPUs. Additionally, storage drives including NVMe SSDs and enterprise-grade HDDs are available. BIOS information can be provided upon request.
Redundancy
Bare metal servers are linked to load-balanced distribution routers, which autonomously facilitate failover processes for networking equipmen
Architecture Diagram
The provided architectural diagram offers a comprehensive overview of our system, with a focus on the essential components comprising our network and infrastructure.
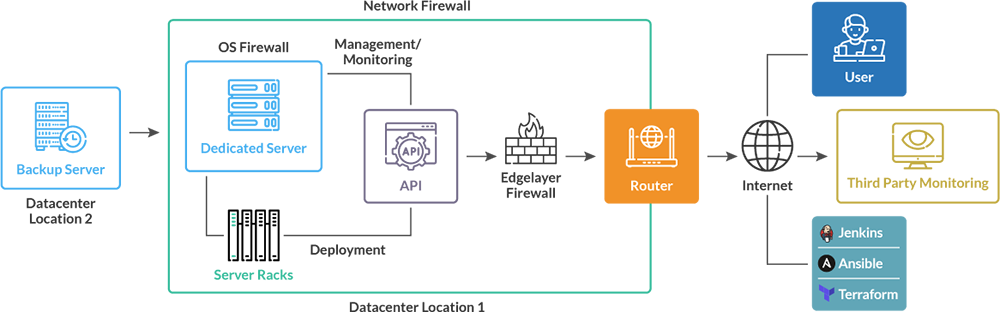
Network Configuration
Connectivity
ISPs like Comcast, Telia TiNet, China Telecom, GTT, and Hurricane Electric connect to our edge layer routers, ensuring optimized traffic delivery.
Edge Routers
Our Edge routers are equipped with security features designed to detect potential threats. In cases where malicious activities are identified, the edge router directs the traffic to the nearest scrubbing facility for the purpose of filtering.
Firewall & POPs
Our Scrubbers segregates illegitimate or harmful traffic from legitimate data, ensuring that only the clean and secure traffic is permitted to continue through the edge router. Utilizing the features of the edge router, users have the capability to create detailed Access Control Lists (ACLs) that filters specific traffic patterns, allowing for effective management of network access permissions. They can also make rules on their devices (OS) to control the incoming traffic.
Software and OS Installation
Operating Systems
We provide options for Red Hat Enterprise Linux (RHEL)/CentOS/AlmaLinux, Debian, FreeBSD, and Ubuntu Linux. Windows server editions are also available.
Control Panels
Control panels offer a graphical user interface (GUI) that provides in-depth control of the operating system, thereby reducing the time and training necessary to manage a bare metal server. The available control panels include DirectAdmin, Plesk, and cPanel
Security Measures
Network Security
Advanced network traffic analysis, vigilant enterprise-grade applications, and robust DDoS safeguards form the foundation of our network security. Technologies like rate limiting, traffic scrubbing, and content delivery networks (CDNs) are leveraged for DDoS protection.
Machine-level Security
Implementation of user access control with strong authentication mechanisms and least privilege principles, firewall configurations to filter traffic, antivirus/antimalware installation, secure OS configurations, and application whitelisting.
Backup and Recovery
RAID
Combines multiple drives into an array to provide a balance between performance and data protection.
Backup Solutions
Third-Party Enterprise Application offers features like incremental backups, block-level backups, and support for various platforms. Additionally, geographically located backups ensure data remains accessible even in the event of a localized disaster.
Scalability and High Availability
Design Principles
Our infrastructure is designed to seamlessly integrate multiple geographical locations for bare metal servers, enhancing both performance and redundancy. This capability provides clients with a straightforward option for deploying their services across multiple locations, ensuring optimal performance and increased resilience.The architecture is built with performance optimization, security integration, maintainability, flexibility, automation, and redundancy as foundational principles.
Backup Servers
Geographically Distributed Backup Servers offer redundancy and act as failover points, ensuring high availability.
High Availability
High availability configurations ensure uninterrupted service by using redundancy and failover mechanisms, minimizing downtime and enhancing system reliability. They typically involve multiple servers or data centers, offering seamless continuity in the event of hardware failures or other disruptions. There are two popular type of high availability configurations.
- Active-Active: Both systems are active and share the load, providing redundancy and load balancing.To read more, please follow the link Active-Active Configuration
- Active-Passive: One system (active) handles traffic while the other (passive) remains on standby, taking over in case of failure. To read more, please follow the link Active-Passive Configuration
Maintenance and Monitoring
API and Database Management
An API server acts as a centralized information repository, holding up-to-date hardware records. This facilitates quick client requests and data retrievals.
Automation Tools
The architecture employs tools like Jenkins, Terraform, and Ansible to enhance the automation of deployment processes, reducing errors and accelerating deployment lifecycles.
Conclusion
This comprehensive framework seamlessly integrates components and techniques to ensure robust, secure, and redundant deployment within our organization's infrastructure. The architecture's emphasis on security, high availability, and automation underscores our commitment to delivering optimized services.




