Serious New DDoS Attack Method Surfaces; Threatens Internet Providers, Businesses
- Category: DDoS
- Author: Admin
- Publisher:
Psychz Networks
- July 21,2015
A new type of crippling DDoS (Distributed Denial of Service) attack on computer networks has recently surfaced. Attackers have been using a previously-unseen method of launching so-called reflection attacks, targeting RPC Portmapper servers. These new attacks have been primarily aimed at companies and hosting providers serving the gaming industry, and were first detected by Level 3 Communications, a major service provider which operates one of the Internet’s top-level networks.
DDoS attacks can best be visualized as artificially-created floods of traffic designed to overwhelm the target machines by using up their resources, leaving no resources remaining for normal server functions. Reflection attacks like this new RPC Portmapper abuse are even more insidious, because they make use of what is known as traffic amplification, simultaneously using a number of third-party machines to dramatically increase the disruptive effect of the artificial traffic infusion.
The parties responsible for the attacks apparently began testing their approach during June of 2015, with larger beta tests seen in mid-August, according to Level 3. The company’s chief security officer believes use of the Portmapper scheme is still in its infancy but has the potential to become as serious as the Network Time Protocol (NTP) DDoS attacks several years ago. In those incidents, hackers used traffic amplification techniques to exploit the core service used across the Internet to synchronize clocks, and caused several of the largest Internet disruptions in history. It was months before a patch was developed to halt the attacks.
Portmapper is an ideal target for hackers looking to launch attacks via traffic amplification. Its purpose is to act as a “traffic cop” of sorts, facilitating network file sharing by telling clients where they can find the networking services they’re looking for. The DDoS originates when a data packet is sent simultaneously to an enormous number of Portmapper servers, using a fake “return” IP address – the address of the attack target. All of those servers send back what they consider to be innocuous responses to the query, but the responses can add up to an inflow of traffic which can overwhelm and disable an entire network.
This type of service disruption caused by reflective DDoS attacks can be extremely expensive. A report commissioned by the information services company Neustar estimates that major financial institutions hit by DDoS attacks can lose as much as $100,000 per hour due to the server issues caused. A similar survey by Incapsula, studying DDoS effects on all North American companies, puts that figure closer to $40,000. Banks and other financial installations (such as ATM networks and point of sale systems), and companies specializing in gaming, Internet operations and hosting are most often targets of the attacks.
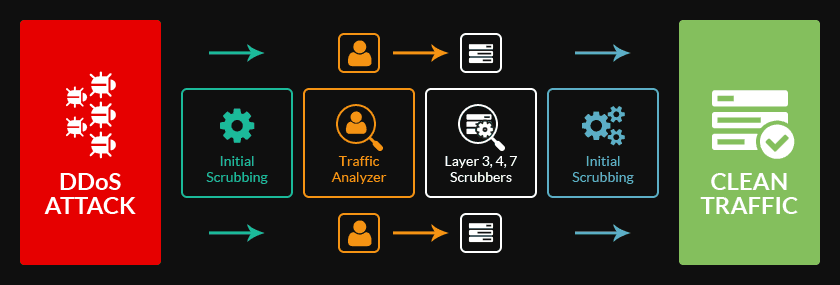
Fortunately for businesses and internet service providers, the Portmapper attacks are much easier to counter than the 2014-2015 NTP attacks. Psychz Networks, one of the nation’s largest Tier4 providers and a leader in DDoS protection, says that it has been able to prevent impact to clients by closely monitoring traffic patterns, disabling Portmapper’s exposure to the open Internet if not required, and rigidly protecting the IPs which are able to contact Portmapper services. Psychz Networks offers what it calls Psychz True DDos mitigation, which it says maximizes client uptime through rigorous inspection, analysis and filtering of all incoming traffic for in-house hardware, as well as remote DDoS protection for network hardware outside of its datacenter.
The early discovery of these RPC Portmapper exploits may prevent the type of widespread problems which caused by the NTP attacks. Level 3 says that to this point, the number of DDoS attacks via Portmapper have been relatively minor, making this a crucial period for Internet service providers to take preventative steps, and for businesses to ensure that their hosting companies provide comprehensive DDoS prevention and mitigation services.